逆向笔记
PE是windows下的文件,ELF是linux/unix下的文件
packer壳
28537194573619560LL LL->长长整型
可在汇编语言中寻找到mov rax ,指针 沿着指针 再按R看转换后的内容(由于低尾端,栈地址向低地址扩展,所以要将字符串反过来)
GDB
b 函数名
下断点breakpoint
b __libc_start_main #在主函数设置断点
set
set $eip=地址 #跳转到某函数地址
set $eip=0x0804849b
r
run 运行到我们下断点的地方,停止
n
运行一步
x/200wx $寄存器
x:就是用来查看内存中数值的,后面的200代表查看多少个,wx代表是以word字节查看看,$eax代表的eax寄存器中的值
反编译pyc
uncompyle2 -h
==md5(md5($pass)) :第一次加密后,结果转换成小写,对结果再加密一次.解密为:解密一次后,再解密一次==
Re2-cpp-is-awesome
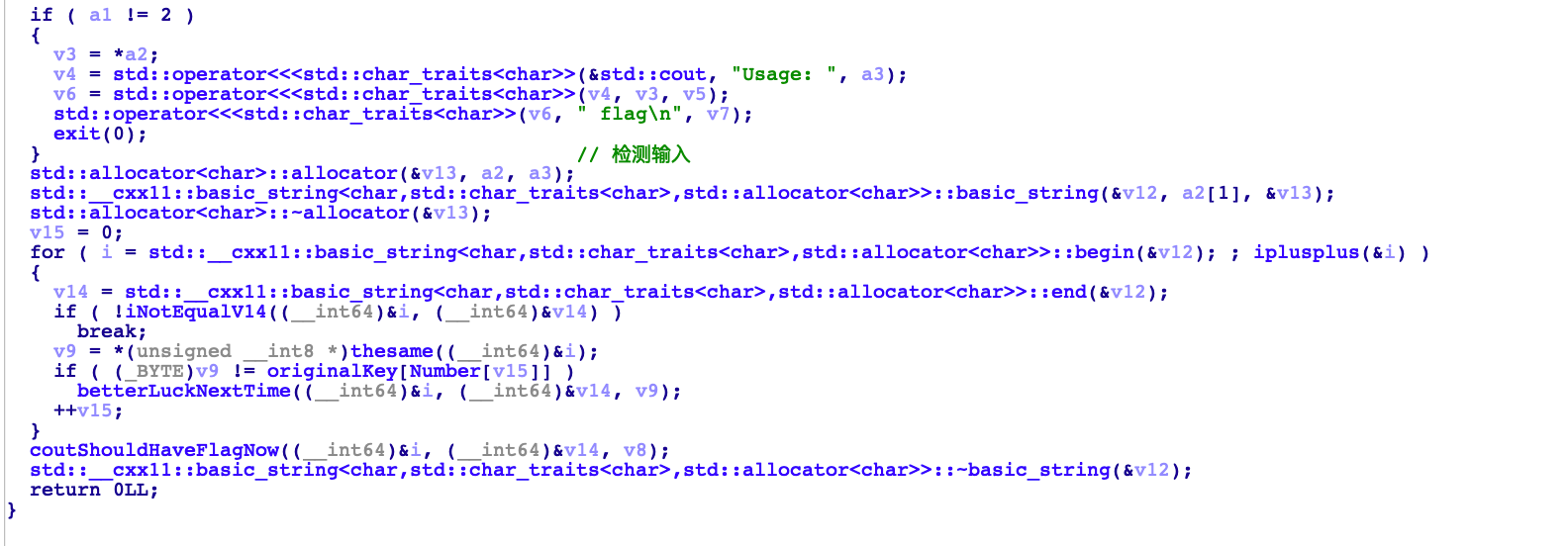
if ( a1 != 2 )
{
v3 = *a2;
v4 = std::operator<<<std::char_traits<char>>(&std::cout, "Usage: ", a3);
v6 = std::operator<<<std::char_traits<char>>(v4, v3, v5);
std::operator<<<std::char_traits<char>>(v6, " flag\n", v7);
exit(0);
} // 检测输入
std::allocator<char>::allocator(&v13, a2, a3);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::basic_string(&v12, a2[1], &v13);
std::allocator<char>::~allocator(&v13);
v15 = 0;
for ( i = std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::begin(&v12); ; iplusplus(&i) )
{
v14 = std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::end(&v12);
if ( !iNotEqualV14((__int64)&i, (__int64)&v14) )
break;
v9 = *(unsigned __int8 *)thesame((__int64)&i);
if ( (_BYTE)v9 != originalKey[Number[v15]] )//key
betterLuckNextTime((__int64)&i, (__int64)&v14, v9);
++v15;
}
coutShouldHaveFlagNow((__int64)&i, (__int64)&v14, v8);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(&v12);
return 0LL;
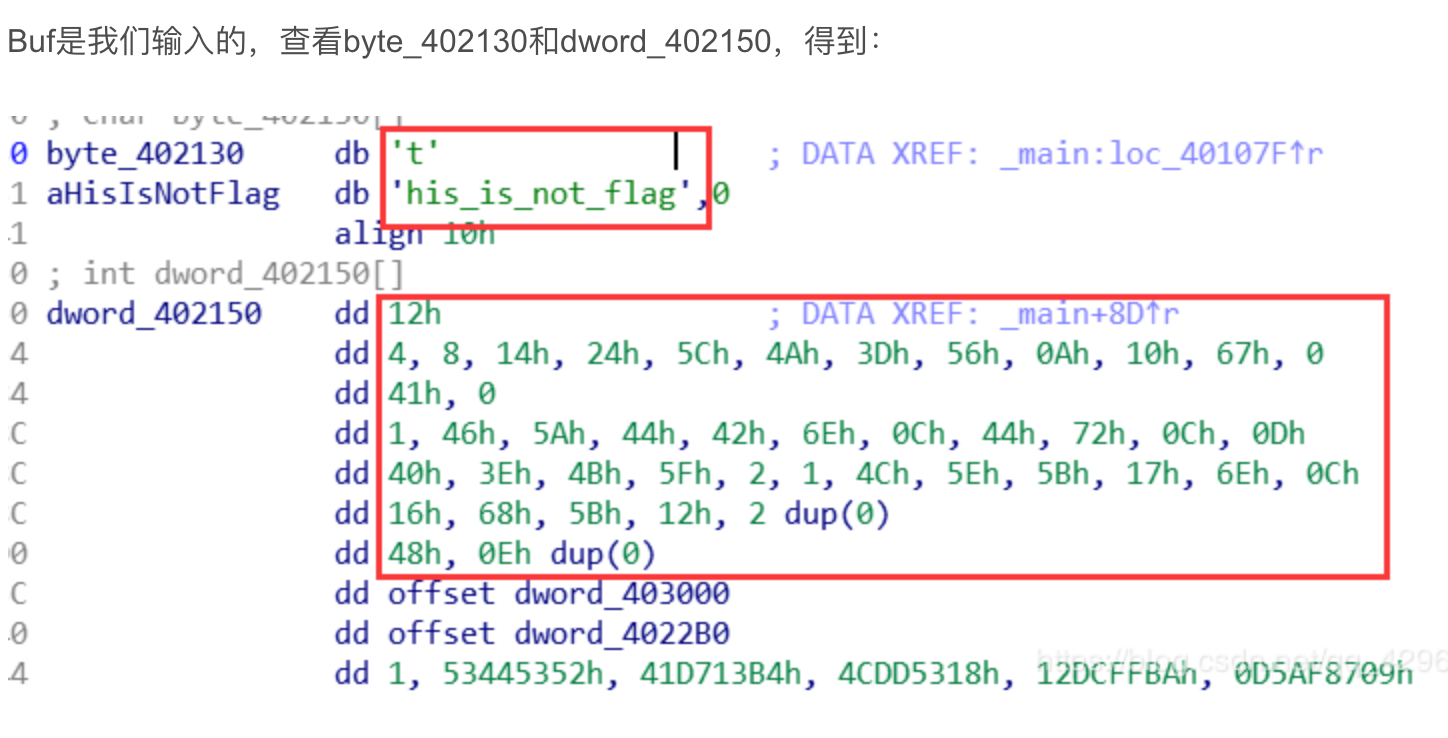
key = 'L3t_ME_T3ll_Y0u_S0m3th1ng_1mp0rtant_A_{FL4G}_W0nt_b3_3X4ctly_th4t_345y_t0_c4ptur3_H0wev3r_1T_w1ll_b3_C00l_1F_Y0u_g0t_1t'
dump = [0x24,0x00,0x05,0x36,0x65,0x07,0x27,0x26,0x2D,0x01,0x03,0x00,0x0D,0x56,0x01,0x03,0x65,0x03,0x2D,0x16,0x02,0x15,0x03,0x65,0x00,0x29
,0x44,0x44,0x01,0x44,0x2B]
flag = ''
for i in dump:
flag +=key[i]
print(flag)
记得全都要写下来,包括0

不止可能是保存,还有可能读取文本中的字符串与程序里的对比
IDA
快捷键Y 输入 char a[0x大小] 就可以自动转成字符串
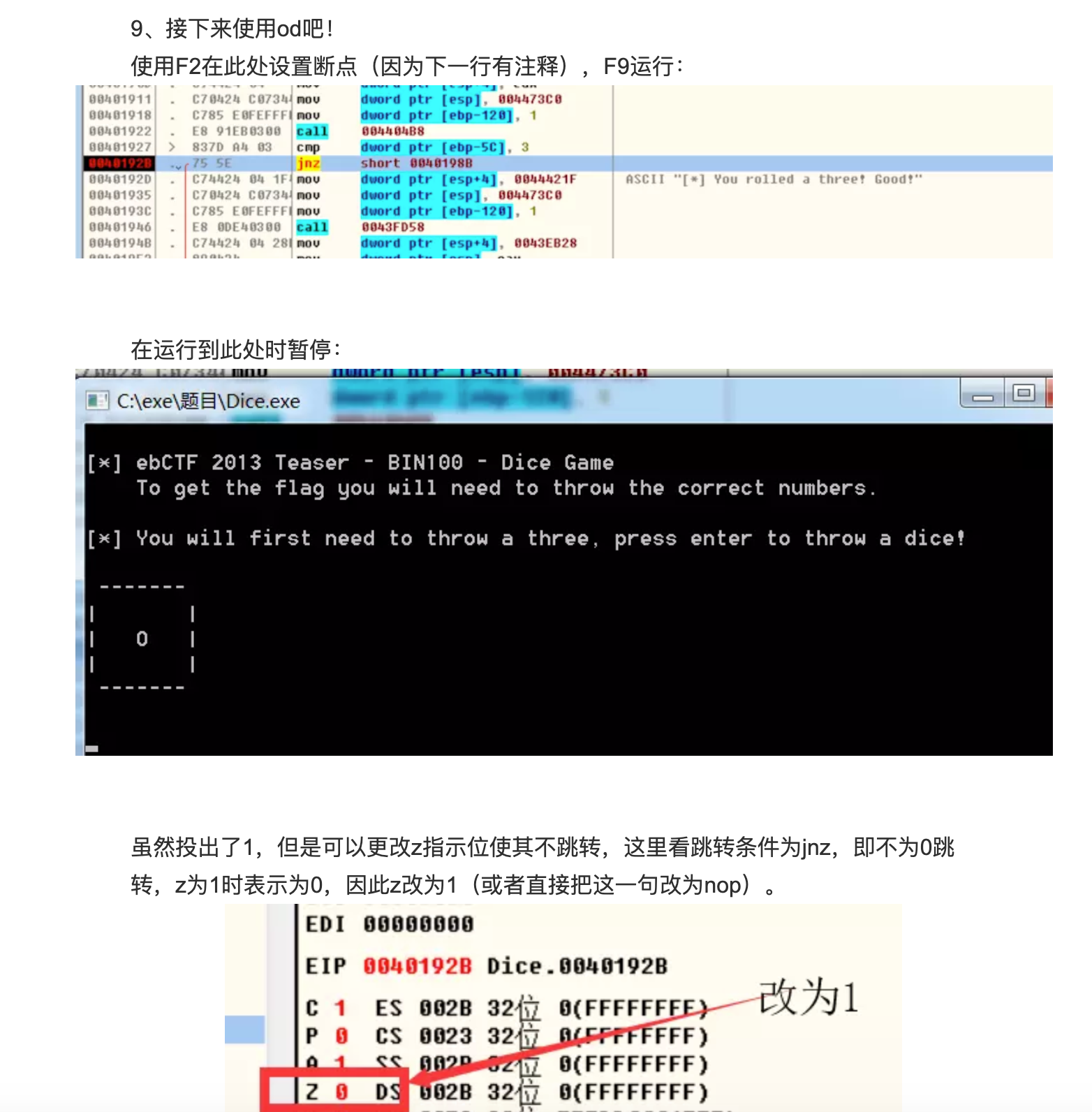
汇编的条件跳转指令:
jmp :无条件跳转 (jump)
je/jz :结果为0跳转 (jump zero)
jnz/jne: 结果不为0跳转 (jump not zero)
js:结果为负跳转 (Jump if sign)
jns:结果为正跳转(Jump if not sign)
jb:小于则跳转(Jump below)
jnb:大于或等于则跳转(Jump not below)
大小端!!!!!!

mercedes!!!!
搜索字符串
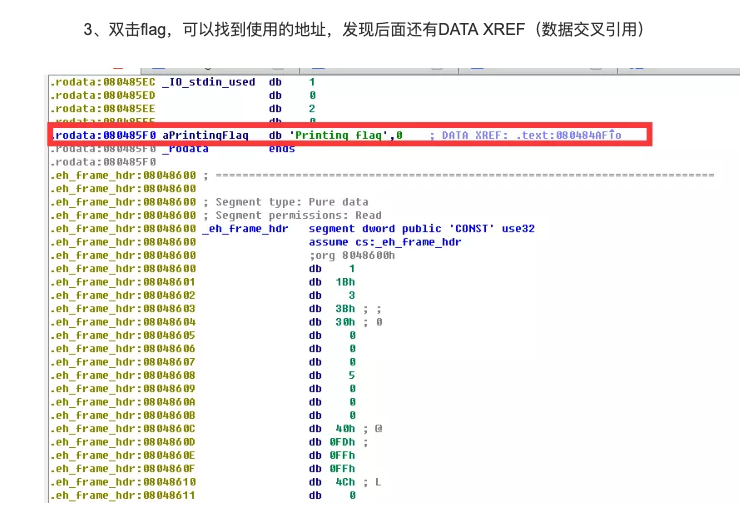
双击flag可找到使用地址
继续双击DATA XREF后面的信息可跳转到命令起始地址
链表https://www.jianshu.com/p/7779f3e83384
https://www.cnblogs.com/ha2ha2/p/7943339.html
ext3
mount filename /mnt/
cd /mnt/
find | grep 'flag'
kali
pdftotext filename.pdf 1.txt
隐写
用chrome打开pdf 复制所有字符 A.B-
逐帧查看,或者使用stegslove
「真诚赞赏,手留余香」
真诚赞赏,手留余香
使用微信扫描二维码完成支付
